In this article I will describe how to setup an OpenLDAP Server and use it to authenticate SSH-Logins in your domain.
What is OpenLDAP
OpenLDAP is a directory service, similar to the MS Active Directory. Here you can centrally manage permissions for the whole network. For example, you can log in to all devices in the network with the same credentials.
In my case I use the LDAP to create a user with sudo-privileges in all containers to be able to connect via SSH. To ensure security, I use only public keys for the SSH login.
OpenLDAP Installation
First of all we have to install the OpenLDAP Server.
apt update
apt upgrade
sudo apt install slapd ldap-utils
Then create an administrator password for your domain.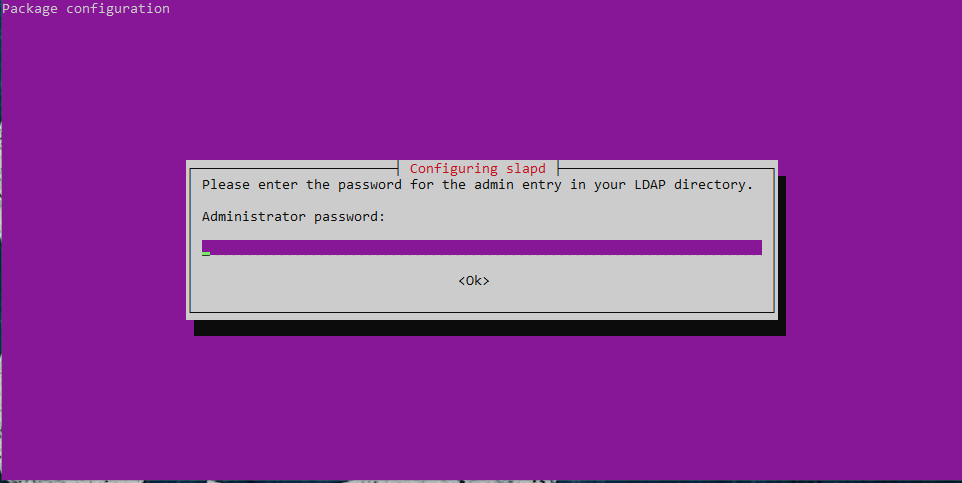
After that recall the configuration menu to add further details.
dpkg-reconfigure slapd
 Select
Select no
 Choose your domain name.
Choose your domain name.
 Choose your organization name. It is usually identical to you domain name.
Choose your organization name. It is usually identical to you domain name.
 Set your admin-password again.
Set your admin-password again.
 Now choose if you want you domain-database to get deleted if you uninstall the ldap-server. I choose
Now choose if you want you domain-database to get deleted if you uninstall the ldap-server. I choose no. That way in case I reinstall the server, I will not lose my data.
Next we have to create Objects in our organization. You can do that via the command line or a webinterfaces like phpLDAPadmin.
phpLDAPadmin Installation
phpLDAPadmin gives you a webinterface to configure you OpenLDAP.
You need a webserver to run it. I will use the Apache httpd.
apt install apache2
apt install php php-ldap php-xml
After that downlaod the latest release from GitHub.
Unzip it and move it into the root-directory of you webserver.
unzip 1.2.6.3.zip
mv 1.2.6.3 /var/www/html
Once that is done, copy the example-config and edit it to match your LDAP-Organization.
cp /var/www/phpldapadmin/config/config.php.example /var/www/phpldapadmin/config/config.php
vim /var/www/phpldapadmin/config/config.php
# $config->custom->appearance['timezone'] = 'Australia/Melbourne';
$config->custom->appearance['timezone'] = 'Europe/Berlin';
$servers->setValue('server','name','My LDAP Server');
$servers->setValue('server','name','JRehkemper LDAP');
# $servers->setValue('login','bind_id','cn=Manager,dc=example,dc=com');
$servers->setValue('login','bind_id','cn=admin,dc=jrehkemper,dc=de');
Now open a webbrowser and navigate to your servers ip or dns-name. You should see phpLDAPadmin.
Now create users and other resources as neede.
Client Authentication
Next we will enable our client to use LDAP-Users for authentication.
First install the required packages.
sudo apt install libnss-ldap libpam-ldap ldap-utils
Go through the wizard and enter your LDAP-Information.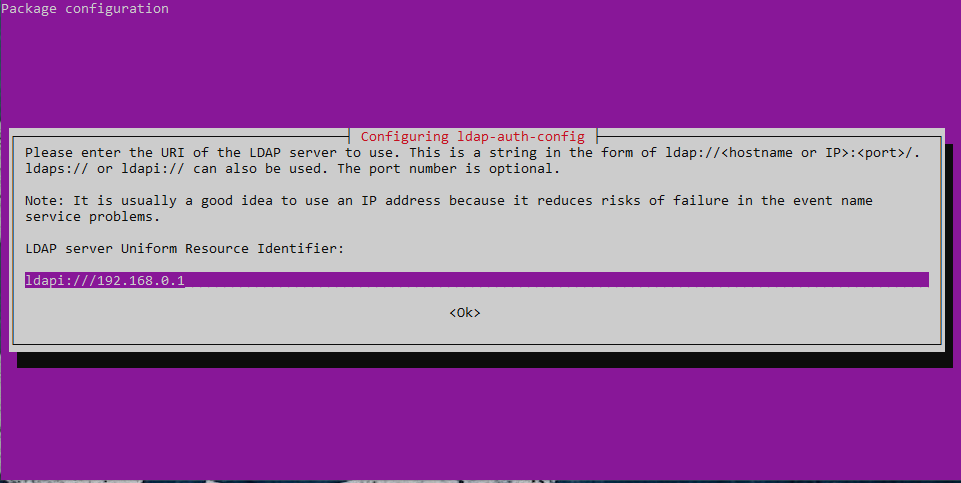
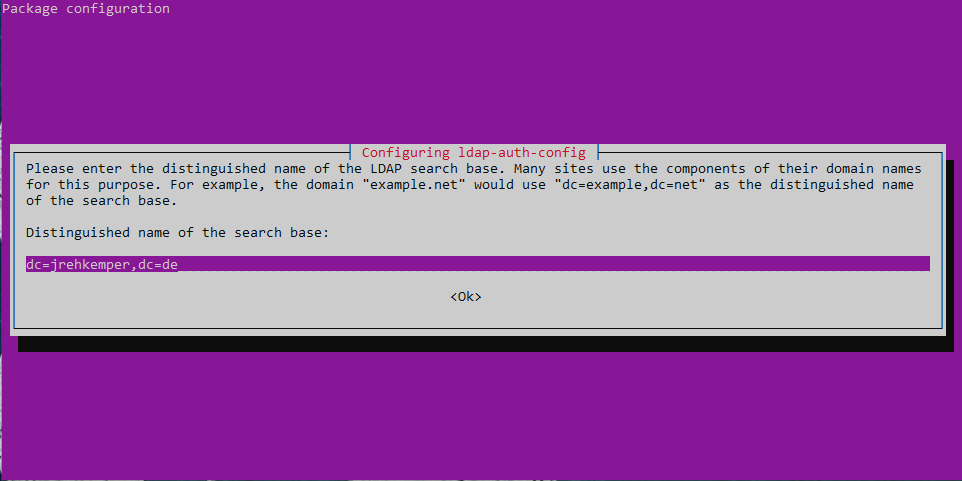
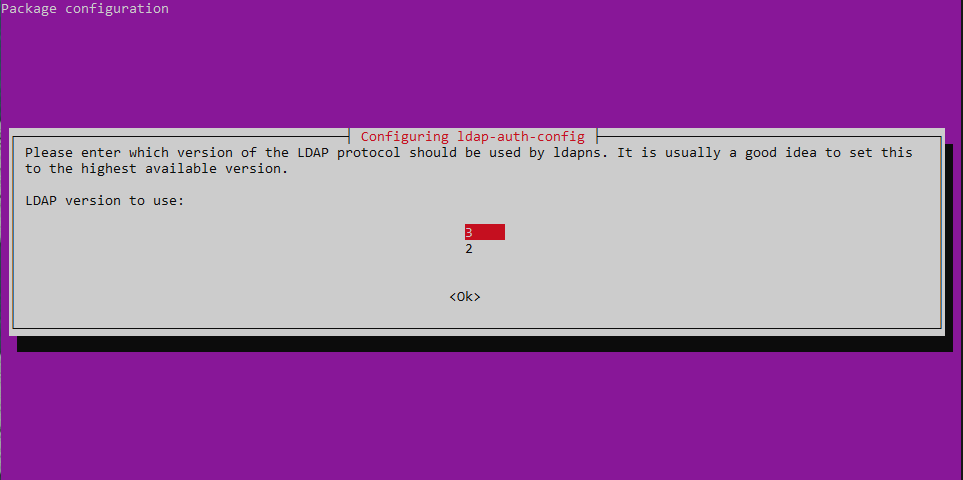
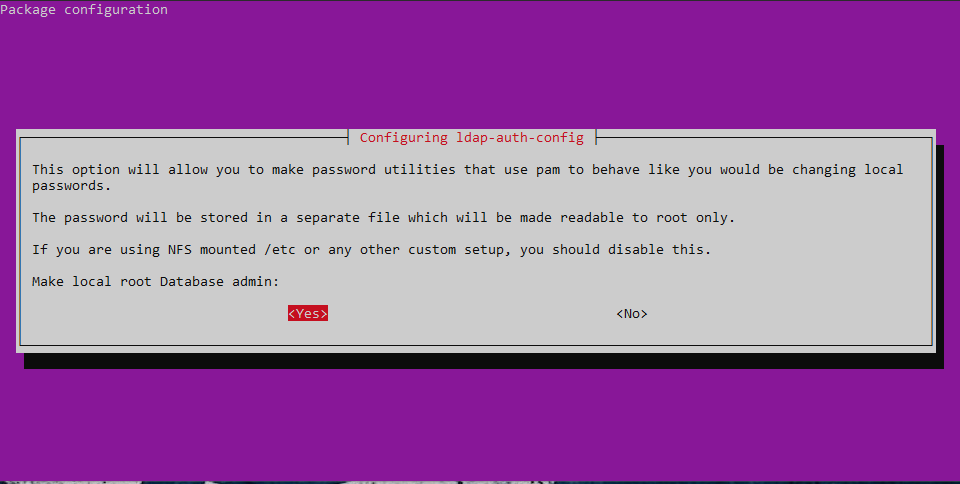
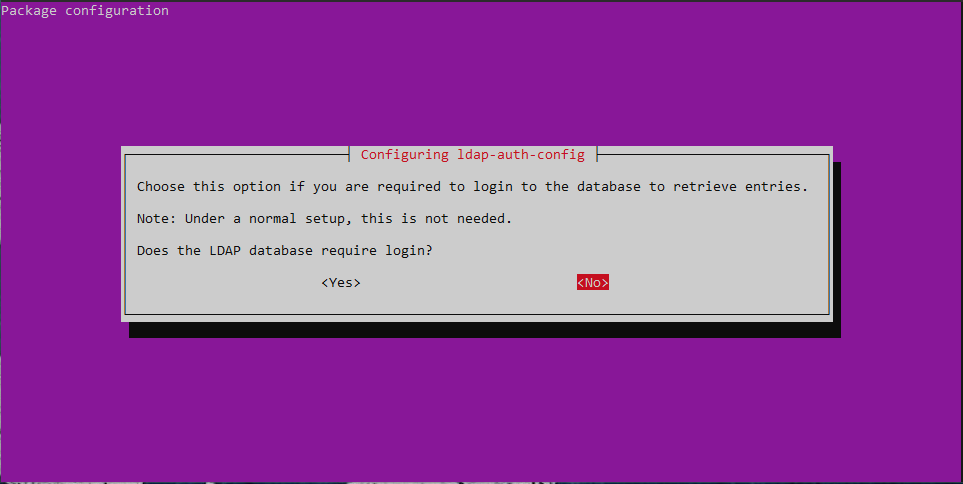
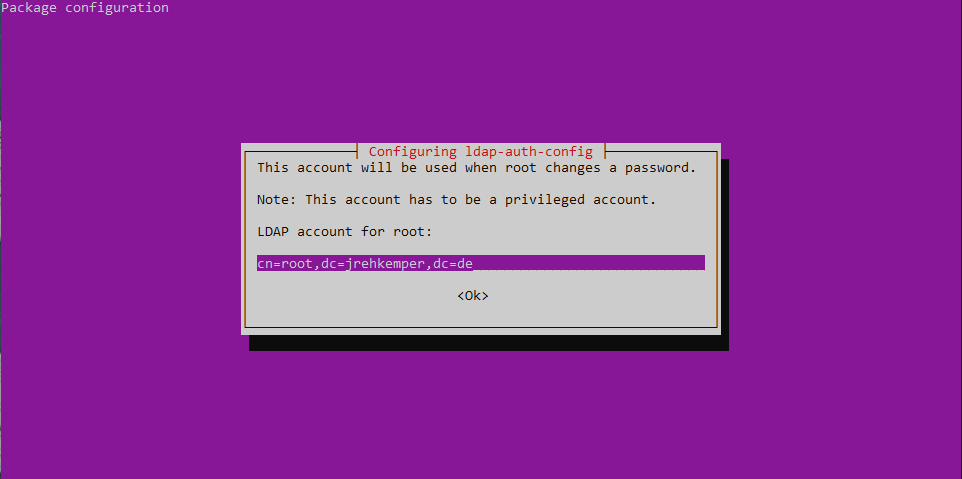
All the settings get saved int /etc/ldap.conf. You can change them there if needed.
Next we add ldap as an authentication option for Ubuntu.
vim /etc/nsswitch.conf
# add ldap
passwd: files systemd ldap
group: files systemd ldap
Next remove use_authtok from the /etc/pam.d/common-password.
vim /etc/pam.d/common-password
# before
password [success=1 user_unkown=ignore default=die] pam_ldap.so use_authtok try_first_pass
# after
password [success=1 user_unkown=ignore default=die] pam_ldap.so try_first_pass
At last we need to edit /etc/pam.d/common-session to create a homedirectory for ldap-users at login.
session option pam_mkhomedir.so skel=/etc/skel umask=077
Add Sudo Group for LDAP
To give sudo permissions to an LDAP user, we need to create a group in LDAP. In my case I call it ldapsudo-
On the client the /etc/sudoers.d/ldap file has to be modified. Here the group from the LDAP must be inserted at an arbitrary place.
vim /etc/sudoers.d/ldap
%ldapsudo ALL=(ALL:ALL) ALL
If you are already logged in as an ldap-user you need to logoff and log in again for the group to get loaded.
Use SSH-Keys for LDAP-Users
Even better than an SSH login with password is the login with a public key. To do this, you store the public key of the client from which you want to access the server in the LDAP. With the SSH login the client sends the own key and the server can check in the LDAP whether this fits to the public key deposited in the LDAP.
In the first step the schema of the LDAP server must be adapted.
For this we first create the following file.
vim /etc/ldap/schema/openssh-ldap.schema
attributetype ( 1.3.6.1.4.1.24552.500.1.1.1.13 NAME 'sshPublicKey'
DESC 'MANDATORY: OpenSSH Public key'
EQUALITY octetStringMatch
SYNTAX 1.3.6.1.4.1.1466.115.121.1.40 )
objectclass ( 1.3.6.1.4.1.24552.500.1.1.2.0 NAME 'ldapPublicKey' SUP top AUXILIARY
DESC 'MANDATORY: OpenSSH LPK objectclass'
MUST uid
MAY sshPublicKey
)
Now add it to your LDAP-Server.
ldap-schema-manager -i /etc/ldap/schema/openssh-ldap.schema
Now we have to store a public key for our LDAP user.
I use the interface of PhpLdapAdmin for this.
To do this, select the user and click on add attributes in the objectClass area. There you select the item ldapPublicKey. After that you can add a new attribute. In the dropdown select sshPublicKey. Now there is a new section below where you can add the public key. If you want to add more than one public key, just click on Add.
Now the public key is stored in the LDAP, but the server needs a way to retrieve it. For this I use the following Lua script from GitHub.
You need to install some dependencies.
apt install lua-5.3
apt install lua-ldap
Furthermore you need to set you LDAP-Server in the config-file of the ssh-getkey-ldap-script.
vim /etc/ssh/getkey-ldap.conf
host=192.168.0.1
base=dc=jrehkemper,dc=de
After that add the AuthorizedKeysCommand to your ssh-server configuration.
vim /etc/sshd/sshd_config
# before
#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody
# after
AuthorizedKeysCommand /usr/local/bin/ssh-getkey-ldap
AuthorizedKeysCommandUser nobody
Now you can login with an ssh-key deposited in you OpenLDAP.
Setup-Script for more clients
If you want to save yourself some work, you can configure additional clients with a script like this one.
Just keep in mind to change it to your values.
#!/bin/bash
echo "####"
echo "Updating System"
echo "####"
sudo apt update
sudo apt upgrade -y
echo "####"
echo "Installing Dependencies"
echo "####"
sudo DEBIAN_FRONTEND=noninteractive apt install libnss-ldap libpam-ldap ldap-utils -y
echo "####"
echo "Changing LDAP Configs"
echo "####"
if [[ -f /etc/ldap.secret ]]
then echo "" >> /dev/null
else
echo -n LDAP Password of Root:
read -s password
echo
echo $password > /etc/ldap.secret
fi
sed -i 's/#host 127.0.0.1/host 192.168.0.1/g' /etc/ldap.conf
sed -i 's/uri ldapi\/\/\//uri ldapi\/\/\/192.168.0.1/g' /etc/ldap.conf
sed -i 's/base dc=example,dc=net/base dc=jrehkemper,dc=de/g' /etc/ldap.conf
sed -i 's/rootbinddn cn=manager,dc=example,dc=net/rootbinddn cn=admin,dc=jrehkemper,dc=de/g' /etc/ldap.conf
echo "####"
echo "Adding sudo Group"
echo "####"
if grep "%ldapsudo ALL=(ALL:ALL) ALL" /etc/sudoers
then echo "done" >> /dev/null
else echo "%ldapsudo ALL=(ALL:ALL) ALL" >> /etc/sudoers
fi
echo "####"
echo "Edit SSH Config"
echo "####"
sed -i 's:#AuthorizedKeysCommand none:AuthorizedKeysCommand /usr/local/bin/ssh-getkey-ldap:g' /etc/ssh/sshd_config
sed -i 's:#AuthorizedKeysCommandUser nobody:AuthorizedKeysCommandUser nobody:g' /etc/ssh/sshd_config
systemctl restart sshd
echo "####"
echo "Setup SSH-Key Script"
echo "####"
sudo apt install lua5.3 lua-ldap -y
cd /tmp/
git clone -b v0.1.2 https://github.com/jirutka/ssh-getkey-ldap.git
cd ssh-getkey-ldap
sudo ./install
sed -i 's:host localhost:host 192.168.0.1:g' /etc/ssh/getkey-ldap.conf
sed -i 's:base ou=People,ou=example,c=org:base dc=jrehkemper,dc=de:g' /etc/ssh/getkey-ldap.conf
cd /root
sudo rm -r /tmp/ssh-getkey-ldap
echo "####"
echo "Configure LDAP Login"
echo "####"
sed -i 's/files systemd/files systemd ldap/g' /etc/nsswitch.conf
sed -i 's/use_authtok/ /g' /etc/pam.d/common-password
if grep "session optional pam_mkhomedir.so skel=/etc/skel umask=077" /etc/pam.d/common-session
then echo "done" >> /dev/null
else echo "session optional pam_mkhomedir.so skel=/etc/skel umask=077" >> /etc/pam.d/common-session
fi
